As on October 2016, Microsoft has published more than hundred security bulletins. The bulletins addresses around 300+ vulnerablities. Out of these three hundred, two hundred are rated as high risk vulnerabilities, more than fifity as medium and low risk vulnerabilities are below fifty. The below graph gives the vulnerability distribution for the last ten months.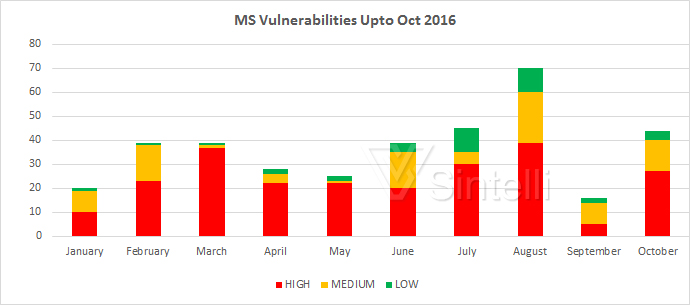
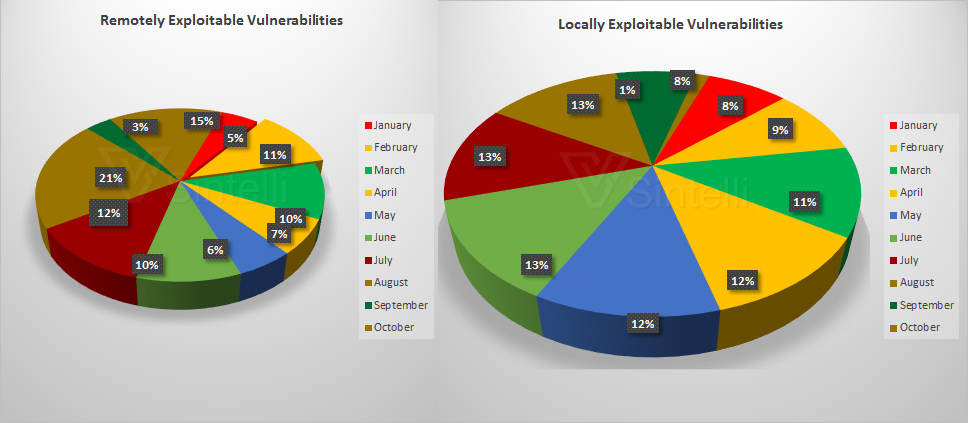
After classifying the vulnerabilites, we found that remotely exploited vulnerbilities are higher than the locally exploitable ones. In August, the highest number of remotely exploited vulnerabilities were released. The below graphs gives a clear view about it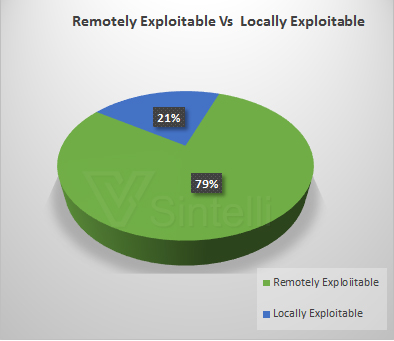
Another important classification is based on the authentication factor. The vulnerabilites that requires authentication (while exploiting the vulnerability) are much less compared to the vulnerabilities that does not required an authentication. In the month of February, March, April and July , there were no vulnerabilities that required authentication for successfully exploiting. The below graph gives a deailed view on this.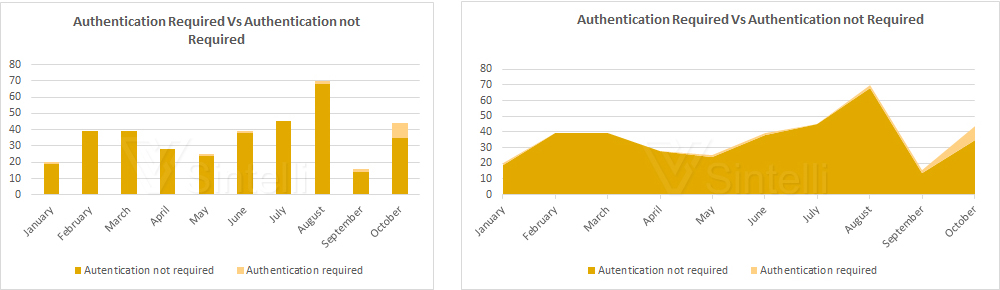
Last but not the least, the very important classification is to differntitate the vulnerabilites with respect to the affected softwares. There are vulnerabilities affecting Internet Explorer , Microsoft Office and other Windows. The below graphs shows statistics based on these three softwares.
This is the overall view about vulnerabilitles affecting various Microsoft products that was released via MS Security Bulletins by the Microsoft. Overall 80% vulnerabilities are remotely exploited and more than 90% of vulnerabilities can be exploited without user authentication.
Microsoft Security Patches : January 2016 to October 2016
- Details
- Written by Dhanyasree
